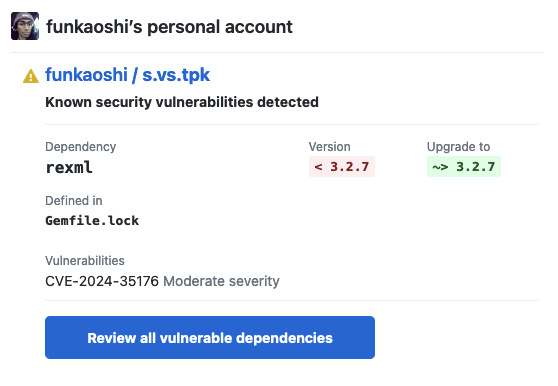
I love that Dependabot automagically lets me know there are vulnerabilities in libraries i’m using. Where tooling like this falls down is the complete lack of context about the program I’ve built. rexml is a dependency of jekyll, a static site generator. I run jekyll locally on my machine, and it generates static HTML files I copy to a server. There isn’t an exploit of interest here. Even if there magically was, the impact isn’t particularly exciting: a DoS when regenerating my D&D blog. I would forgive someone for tuning out the messages from Dependabot, because the serious can end up mixed together with the so-so.
You have a similar issue with the results from code scanners. It’s easy for those tools to misunderstand the impact of what you’ve written. Certainly every interaction I’ve had with them has involved looking at their output to first figure out what’s a legit finding. I am sure many developers have had to fix non-issues to placate 3rd parties who treat the output of these tools as sacrosanct.
I have no pithy conclusion to this post: doing application security well is difficult.
